Just having lost about a week debugging a potentially major issue, I’ve decided to share a few insights, to potentially save others the time I, we, just wasted: FortiVPN Auth with SSO shows a strange email address and redirects to login.live.com.
The Scenario
A user opens his FortiVPN Client, selects the correct profile, configured to use SSO, clicks connect and waits for the branded SSO window to appear. Here he is requested to enter his email address, which he does and clicks login. Strangely, instead of requesting the user’s password, it shows a login.live.com login window and asks for the confirmation of a Russian email address (dm*****@chuverin.msk.ru).
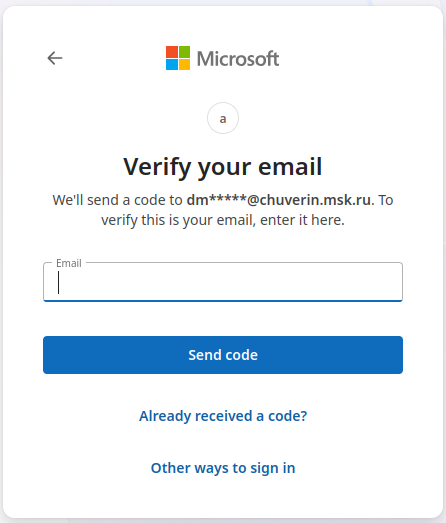 The companies EDR solution is utilized to scan the device, logs are analysed, traffic checked. Nothing. The issue is not reproducible, so the system is put on a watch list.
The companies EDR solution is utilized to scan the device, logs are analysed, traffic checked. Nothing. The issue is not reproducible, so the system is put on a watch list.
A week later it happens again and all steps are repeated without results. To be safe, the device is replaced with a new one. And the old device recalled for forensics.
A week later the same happens again on the new device. F***.
A day later, after discussing with colleagues, a similar issue appears on a different device, just with a @skype.net email address. Again, no traces of anything. It does not happen every time but is reproducible at random.
F*** F*** F***
FortiVPN Logfiles
Analysing the client logs, shows the correct connection to the authentication node, which forwards to login.microsoft.com, which returns the branded form requesting the email address. Next comes a request to login.live.com, which should not be there. There also are no visible reasons for the redirect.
At this point a colleague had already analysed the FortiVPN client’s settings and binaries etc. without results.
FortiVPN CoreWebView2
During a discussion a colleague remembered an auto complete bug in CoreWebView2 and asked whether auto complete had been used, which I couldn’t remember. But….it triggered me to try a little something…
Going to the affiliated SSO page I entered the user’s email address and deleted one character after the other, and after deleting the complete domain including the @, I started seeing existing accounts and was redirected to login.live.com. Having only one character left, I hit the strange email address we had been reported.
It turns out, the auto complete bug, if entering a.name@doma.in, and using auto complete after the a, it will show a.name@doma.in but when clicking next, it will only forward the a. Missing the @doma.in, Microsoft does not identify it as a corporate account, does not forward it using the initial SSO flow, but instead forwards the login request to login.live.com and the first character as a username. Now the live.com account with the username a, belongs to somebody with the email address dm*****@chuverin.msk.ru, which caused our potential incident.
Practically the bug results in the input field showing the complete auto completed text, but only forwards the text, which was in the field, when auto complete was used, as such not necessarily only the first character.
Solving the Issue
The issue might be dependent on using Win11, but in general: update the FortiVPN client or your CoreWebView2. Or don’t use the integrated WebView, but the Browser instead. Ooor don’t use autocomplete! Problem solved :) And, relax, you’ve probably not been hacked, but just lost some time due to a bug!
P.S.
Thanks to the mentioned colleagues!!!!
For completeness
Here is a list of the associated email address of all single character names on login.live.com, so potentially you just reached this page because of that! :)
| username | mail address |
|---|---|
| a | dm*****@chuverin.msk.ru , ja*****@skype.net |
| b | be*****@mac.com |
| c | |
| d | it*****@skype.net |
| e | |
| f | |
| g | |
| h | |
| i | ro*****@gmail.com |
| j | |
| k | it*****@gmail.com |
| l | |
| m | it*****@skype.net , ja*****@skype.net |
| n | |
| o | |
| p | |
| q | |
| r | |
| s | dy*****@gmail.com |
| t | |
| u | |
| v | |
| w | |
| x | |
| y | |
| z |
A note: I’m very sorry to expose these partially anonymized but still private email addresses here. That said, I require it to be necessary, to help others with identifying the bug described above.
And as a Bonus
The following PowerShell script can be utilized to extract FortiVPN related information from a system.
#Get the Desktop's path
$dtpath = [Environment]::GetFolderPath("Desktop")
#Get a current timestamp
$timestamp = Get-Date -Format "yyyyMMdd_HHmmss"
#Set the path of our temporary folder
$fet = "$dtpath\fet$timestamp"
#Create the folder
New-Item -Path $fet -ItemType "Directory"
#Get the FortiVPN installation
##Create a target folder in the temporary folder
New-Item -Path "$fet\ProgramFiles" -ItemType "Directory"
##Copy the folder
Copy-Item -Path "C:\Program Files\Fortinet" -Destination "$fet\ProgramFiles" -Recurse
#Get settings from AppData
##Create target folder for UserLocal
New-Item -Path "$fet\UserLocal" -ItemType "Directory"
##Copy folders from UserLocal
Copy-Item -Path "$env:APPDATA\..\Local\Fortinet" -Destination "$fet\UserLocal" -Recurse
Copy-Item -Path "$env:APPDATA\..\Local\FortiClient" -Destination "$fet\UserLocal" -Recurse
##Create target folder for UserRoaming
New-Item -Path "$fet\UserRoaming" -ItemType "Directory"
##Copy folders from UserRoaming
Copy-Item -Path "$env:APPDATA\Fortinet" -Destination "$fet\UserRoaming" -Recurse
Copy-Item -Path "$env:APPDATA\FortiClient" -Destination "$fet\UserRoaming" -Recurse
#Fetch Registry Entry
##Create target folder
New-Item -Path "$fet\Registry" -ItemType "Directory"
##Extract known Registry Paths
Invoke-Command {reg export 'HKEY_CURRENT_USER\Software\Fortinet' $fet\Registry\hkcu_software_fortinet.reg}
Invoke-Command {reg export 'HKEY_CURRENT_USER\Software\FortiClient' $fet\Registry\hkcu_software_forticlient.reg}
Invoke-Command {reg export 'HKEY_LOCAL_MACHINE\SOFTWARE\FortiClient' $fet\Registry\hklm_software_forticlient.reg}
Invoke-Command {reg export 'HKEY_LOCAL_MACHINE\SOFTWARE\Fortinet' $fet\Registry\hklm_software_fortinet.reg}
#Fetch some general information
echo 'Take me home tonight!' | Out-File -FilePath $fet\general.txt
echo 'Username: $env:USERNAME' | Out-File -FilePath $fet\general.txt -Append
echo 'Domainname: $env:USERDOMAIN' | Out-File -FilePath $fet\general.txt -Append
echo 'Computername: $env:COMPUTERNAME' | Out-File -FilePath $fet\general.txt -Append
echo 'systeminfo!~~~~~~~~~~~~~~~~' | Out-File -FilePath $fet\general.txt -Append
systeminfo | Out-File -FilePath $fet\general.txt -Append
#Create archive
Compress-Archive -Path $fet -DestinationPath $dtpath\fet_$timestamp.zip