In 2016 Bastille’s Research Team published information on the so called MOUSEJACK attack . The attack exploits the lack of encryption between wireless mice / keyboards and the applicable USB dongles. Most available devices from companies like Logitech and Microsoft were vulnerability.
The used attack tools initially sniff traffic between the input device and the dongle and identify the address of the involved parties. Afterwards the input device is spoofed and arbitrary input injected into the dongle, which in return starts controlling the host system. Although there is a pairing between the dongle and the input device, the pairing is only based on address, which are part of the packets.
Bastille Research, MOUSEJACK
Bastille has a few research tools published on GitHub. As the instructions are straight forward, there is no reason to add any further notes.
JackIt
JackIt is simple exploit tool for MOUSEJACK and supports all steps from sniffing down to actual injection. Injection is performed based on Ducky Script which is the scripting language also used by the HAK5 USB Rubber Ducky .
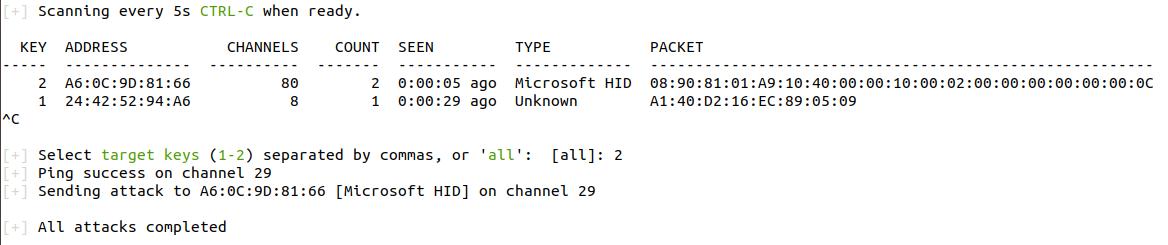
Screenshot
For the following screenshot JackIt is run with jackit --script test.ds. Where test.ds contains STRING blablabla.
Potential Issues
As everybody who has ever tried to inject keystrokes probably painfully knows, there are many different keyboard layouts out there. One of the classic issues here is the swapped of the swapped y and z characters on German vs. English keyboards. For this reason the developers of JackIt have added a --layout function.
Hardware
As described in Bastille’s documentation on their tools, there are various approaches concerning hardware. I personally have a CrazyRadio PA and am very happy with it. I’m not sure were I got it, and it looks like a clone … but they’re available at Seeedstudio and EXP-Tech .
Mitigations
Input Device Side
Mitigations only on input device side will not result any issues. The dongle always has to be adjusted to changed input.
Dongle Side
Mitigations solely on dongle side can be compared to input firewalls. The easiest approach is to only allow valid input, which would defend against keyboard keystroke attacks against wireless mice and presenters. Still this filtering won’t work with keyboards as they need to be able to type.
Both Sides
The “easiest” approach would be to add encryption to the communication. Here of course individual keys would be necessary for each dongle / input device pair. Alternatively a secure pairing mechanism would have to be implemented. The biggest issue here is that for most devices a firmware update on the actual device is not possible without direct physical access. As such, while vendors may be able to update the firmware on a dongle, but probably not on the wireless input device.