type: ‘post’ title: ‘USB Malware’ date: ‘2024-06-22 01:00:01 +0000’ tags: [] author: ‘brian’
A short while ago I needed some real life malware samples to do a PoC related to the infection mass storage devices like memory cards and USB drives. Sadly, while there was a lot of information on the malware, and a few available samples, I wasn’t able to find images of infected drives. Thus…
Disclaimer
Functioning / Live malware can cause significant damage. This also applies to old malware in modern days. Thus, if you don’t know what you’re doing, make sure to do your homework before even trying.
The Malware
For the project I needed to PoC the infection of Mass Storage devices with Conficker , Hilgild , Palevo/Mariposa , Vobfus/Beebone {:target"=_blank"} and a few others. The plan was, in addition to referencing the vast amount of writeups, to show what a dive infected by the malware actually looks like. Which folders/files are added and which data might be overwritten.
Getting samples
As expected, it wasn’t as easy as downloading a single sample each, executing it on an old isolated Win XP Box and inserting the drive. It was rather a question of testing my way through multiple samples, separating actual malware from loaders and finding executables that weren’t just DLLs with undocumented entry points.
Eventually my main source for functiong samples ended up being
VirusShare.com
. I also worked with a few from
Abuse.ch’s MalwareBazar
{:target="_blank} and some that a very good friend was able to share from
VirusTotal
. With VirusTotal also being my goto service for matching the samples against the AV engine’s detections and names.
Results
For details on the files, structures and functionality, have a look at the writeups linked above.
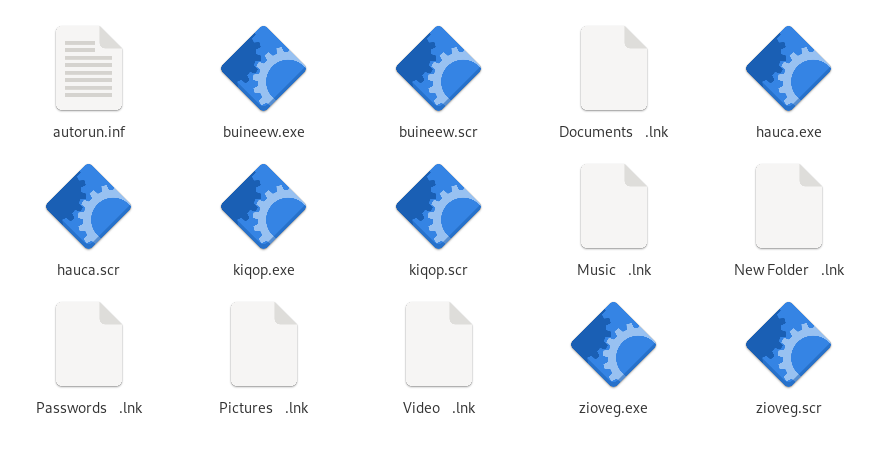
Vobfus
Vobfus creates an autorun.inf with the following content
[autoRuN]
acTioN=�ffnen Ordner, um die Dateien
sheLlExecute=hauca.eXE
ICon=%SysTEmRoOT%\syStem32\shElL32.dlL,4
and a bunch of other binaries and links
f9d55ae606b15bea868689c2ae265111078aab03fd20005d6ef3f9e980b618b5 autorun.inf
b38292f6c9dcab5128e2daad9648e0c0461f865307560d74a59dfa4d6b4d53f8 buineew.exe
afc24bac77a50a91e124d45bc81ccde579daeeb3d9e1682421d30f58366d3893 buineew.scr
b4364f22f806c1978d739692b5f36cff7584133a60247c72569b542b3fb3161d Documents .lnk
75873c13f8c59cca47f821853febf95f80f4c0a32535cbe886e8366e397b13b8 hauca.exe
75873c13f8c59cca47f821853febf95f80f4c0a32535cbe886e8366e397b13b8 hauca.scr
be9951916c81f2ccd9d65e91fa576d664788775b073d3ae85f9a64acb32df381 kiqop.exe
49d3d46aa21628297976e3f96607d0c80c75a4408a23c5f3ab986929013171b5 kiqop.scr
24852ca196d525c96aebb387440dbc57271402dfab119a077d3de1436e1bb8ae Music .lnk
f16551e22ef9eb5f6ce8bf61451ab12457c372f8d6ebd8128e1ba412bb5b55a3 New Folder .lnk
b16589f437ab9c21932e035400512db01808a73e6d5f904cb1e16fbeba5ddc29 Passwords .lnk
264fae23e6531c1f151f31e45ac7a315692489143efe5fb8df73a7d020d90d7b Pictures .lnk
15eaeea6a914b1c72389cf54fc8461bc89afb539220ee534a70f90ab83c6f665 Video .lnk
c4c17e56754a6bfe7cb0e9feba0794ef77ae318573b55d81f9e3fce5d82466d2 zioveg.exe
daba76fa6c7886984b1705f3f9bb25038a7c73085a7ba4f3cdcd51bc3be5c581 zioveg.scr
The links refer to either one of the binaries on the drive.
And a screenshot from the file explorer for quick recognition.
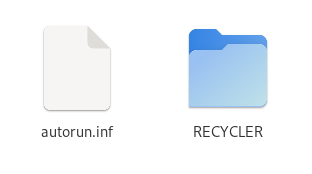
Palevo
Palevo creates both an autorun.inf and a folder called RECYCLER.
autorun.inf contains a bunch of unprintable characters, but can still be read.
;6JmP
;This Program Cannot Be Run In DOS Mode.
;T
;G;hP
[aUTOrUN
;ÿƒÄ
;Hkey
;„Õñ
oPeN=ReCYClER\\explorer.exe
;€ÇEø
;DL/UP
actION=Open folder to view files
;£ 5Ûv
;
;ÄKap
ICoN=shELL32.DlL,4
;ßÿÖ
;9;x;
SHEll\\OPen\\coMMaNd=rECYCLEr\explorer.exe
;M
‹c
;x;F2?
SHElL\\eXPLOre\cOMMANd=rECyCLeR\\explorer.exe
;
ÿ0
The actual payload is stored in the RECYCLER folder
ab25292bd7b97a1b6f1a364633de15970c0381217b7e2c8e9ca0593041b8f971 Desktop.ini
27d84ab6938bf88801dce54fc3d879547a3f6e95a36369316468ab43d2856a01 explorer.exe
And a screenshot from the file explorer for quick recognition.
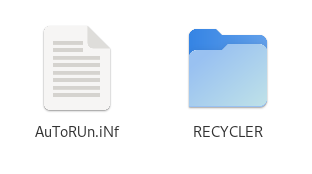
Hilgild
Hilgild, as expected, also creates an AuToRUn.iNf and a folder called RECYCLER. But uses AuToRUn.iNf has a by far longer AuToRUn.iNf.
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
CMCDLLNAME32=mapi32.dll
CMC=1
MAPIX=1
MAPIXVER=1.0.0.1
OLEMessaging=1
[MCI Extensions]
aif=loghours.dll
aifc=psnppagn.dll
aiff=ole2.dll
asf=d3dramp.dll
asx=MPEGVideo2
mpe=usrdtea.dll
mpeg=MPEGVideo
mpg=MPEGVideo
mpv2=idq.dll
snd=atl.dll
wm=mcd32.dll
wma=MP3
wmp=MP4
wmv=MPEG
wmx=MPEGVideo2
25846ki756as
;cc30qiLas JdZ3adCPEadfj823423423
[Kasasf0q]iLasdfjKD28Ls33wDm2rq6Jl1EdAf8
;K0qi asfLasmet Ca19lhs ipconfigdfjKD28 mpeg Ls33
;8sdaA89KL3J0DSKJLG8P34Ld0laH saG
[shellas]dBopncomasdnsdf=fdsjsdf.exenghsadnetstad.
as=asdfasddfsad asdfsafsdfsafdasf
;ff0qiLasJdKPEGVi2412344
oaeFK1Kajkw6DdDL2f3a31zazi8a135Lwra
Ls33wDm2rq6Jl1EdAf8soae FK1Kajkw6DdDLKAl6sdcO7K
asdfsadfLsafdsfadsdm FKajkw6KAl6sdcO7K
;K0qiLaasJdZ3adCsa1sdfjKD2asdsdfasdf
;K0qiLa1Kajkw645rthggK2f3a31zazi8a35Lwra
[autorun]K0qi3adCa19lhsdfjKD2asfd23asdfsdfa
PRINT=PRINT.EXE ASDd1sdaf897asdj
;[asfd3]2KdafjKD2
Play= Copy pictures to a foler on my computer
shEllEXEcuTe = RECYCLER\wmimgmt.exe
;8sdaA8G8P34LklJ8ASD FL333sd0laHsaG12fgsdsaKd
sheLL\oPeN\coMManD =RECYCLER\wmimgmt.exe
;343P5Fsd2fKgCOMNANDASDF=REC R5gf56sd315eK562AdsFSD
;89234SAKDJWKsatyh3adaflk7yas
;343P5F 25F5gf56sd315eK56fs43d4asd56KdaDfs1
shELl\ExpLore\ComMand= RECYCLER\wmimgmt.exe
s=asfdsadffsdafdAf8soaeFExpLoreqiLasJdZ3adC
;89234SAKfdlk28ASDFsaaty7yasK6DRg if5S3jsKHks
Action=Open folder to view files
;8k3kKsafG ASDFdlsflfKa23F4jksfaF3J90s
;f0PEGVideoqiLasJdZ3adCa19lhsdfjKD223asdfasfd
Spell=Take no action then print the picture
[drivers]
wave=mmdrv.dll
timer=timer.drv
[mci]
[driver32]
[386enh]
woafont=app936.FON
EGA40WOA.FON=EGA40WOA.FON
EGA50WOA.FON=KBDSP.FON
The RECYCLER folder is setup as follows
e4eed26254df3fbeb5f5aa4aca78a8c180469a40e8f463311d03123fd215b954 83300042.db
86b51772dc0623666079a31c10b89f027968de029269ed8b6ea1b134dd4c4159 desktop.ini
94b2bc0199a495135acb21133497c9bf2ca4484b5f1fa172a03f4ac67a3eb422 wmimgmt.exe
And a screenshot from the file explorer for quick recognition.
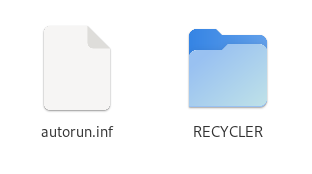
Conficker
Conficker, the same, autorun.inf and RECYLER folder. But, autorun.inf is massive with it’s 59kB which is recognised by
Virustotal with SHA256: dfc1f69b3efc968310ed8901eda055ea40fa488059a6a3763c356539820ccc3e
.
The RECYLER folder contains a further folder called S-5-3-42-2819952290-8240758988-879315005-3665 which contains a single file
014e5c3de74582b5baa34308c2173225b36c4da0999c2b2e0f32d87e4f5b9776 jwgkvsq.vmx
And a screenshot from the file explorer for quick recognition.
Samples
Each zip file contains the raw image of the 64MB memory card I used to create the samples. As the card was mainly empty, the images compress significantly.
The Samples are live, dangerous and only intended for research purposes! Handle with care.
| File | SHA256 |
|---|---|
| conficker.zip | e0f37567b2cd4fe57c6e979634074bf704968fee9e44026dc1cb04c2d79b403d |
| hilgild.zip | 95acce2245bd7a4e714e390d9749e2d03125c44809a060e34968e25318481fa2 |
| palevo.zip | 5f721ea8871266bf2328ebbf6eaac3cdefde3a242a77f7fdef5285e05de13427 |
| vobfus.zip | 82cbe54aed37f2358be14d74a7f1c45ebfd32997cadf1d3bb2327cdc3da1cb17 |
The password ought to be known.